A simplified approach to following the DOD (U.S. Department of Defense) Zero Trust roadmap using Microsoft security solutions.

Introduction
The DoD Zero Trust Portfolio Management Office (ZT PfMO) released the Department of Defense Zero Trust Strategy and Roadmap on Nov 22, 2022. It defined what the DOD needs to do to execute Zero Trust. A new zero trust compliance policy compatible with NIST 800-53 or Security Technical Implementation Guide (STIG).
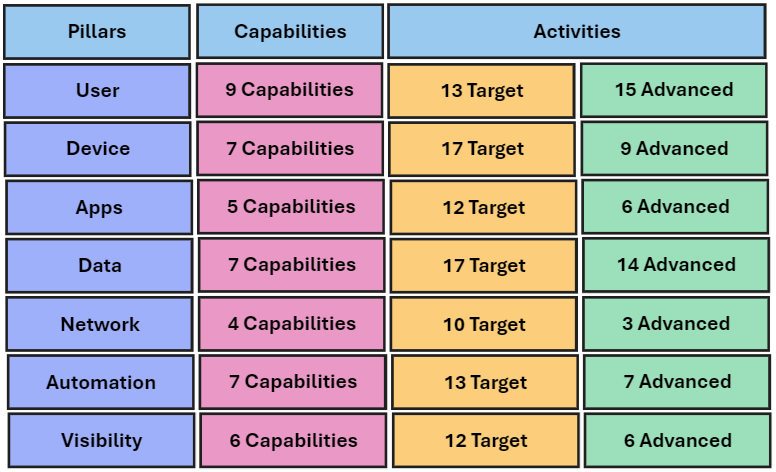
The roadmap is broken into 7 pillars including User, Device, Application, Data, Network, Automation, and Visibility.
These pillars span 45 capabilities. Each capability is defined by one or more activities. These activities can also be target-level or advanced. There are over 150 activities with 92 target activities and 60 advanced activities.
The official implementation timeline for each pillar varies, though the deadline is generally stated as 5-years for target-level (2027) and 7 –years for advanced (2029). Rather than waiting for 5-7 years, DOD organizations are rushing to meet ZT compliance. In many cases these activities may require several years of planning and implementation to achieve.
Each capability tends to follow a path of progression over several activities. Starting with target-level activities like security solution deployment, consolidation, and cloud adoption.
Many capabilities include advanced activities that often include advanced automation, machine learning (anomaly detection), and artificial intelligence. Each capability can have several activities that progressively describe more complex solutions.
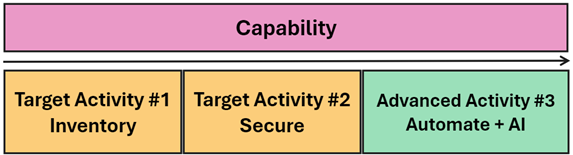
Activities are numbered by pillar, capability, and activity. For example (1.7.1) is the first activity in the 7th capability of the user pillar:

Additional considerations:
- Capabilities are vendor-agnostic descriptions that use terminology and wording that may not directly map to specific vendor products.
- It is critical to consider context when evaluating an activity. Consider the pillar, capability, and target/advanced. Taking activities out of context will cause confusion.
- The ZT roadmap is lengthy and at times imperfect. You may find some activity descriptions difficult to interpret, duplicate, generic, or using unexplained acronyms.
- Interpretations by employees, vendors, consultants, and auditors will certainly vary.
- Many activities are repeated or overlap across multiple pillars.
- Activities may describe procedural and documentation-based solutions.
- A limited number of activities may not apply to all DOD organizations. For example, activities related to BYOD and on-premises (for cloud-only orgs).
- Microsoft has solutions to nearly all DOD Zero Trust technical capabilities with a few limited gaps due to Azure Government feature availability.
- There is no end-state for zero trust. DOD organizations will be on a continuous journey to achieve greater compliance with zero trust. Striving to remediate coverage gaps, increase adoption, expand visibility, standardize configuration, document process/exceptions, enforce compliance settings, and automate manual processes.
Pillar Summary
- User Pillar: Identity in all forms (users, service accounts, keys, certificates, MFA, etc.).
- Centralized, cloud-based identity provider that includes just-in-time-access, least privilege, automated approvals, conditional access, MFA, dynamic risk-based denials (deny by default), identity lifecycle management, alt token support, cloud-based PKI, continuous authentication (each session is repeatedly validated).
- Device Pillar: Device management including configuration, antivirus, and XDR.
- Centralized, cloud-based device management that includes application control, compliance verification, risk scoring, next-gen antivirus, policy enforcement, patching, file integrity monitoring, certificate management, and EDR-XDR.
- Application Pillar: Secure application hosting and development.
- All apps and components are inventoried (SBOM), only authorized apps are allowed, security standards enforced, developed using CICD pipelines, approved repositories, vulnerability-risk management, and continuously monitored.
- Data pillar Data tagging, labeling, data protection, and data loss prevention.
- Data is identified (tagged), tracked, and changes are monitored. This includes encryption, data loss prevention, access management, data loss prevention in a variety of forms and locations (databases, devices, software-defined storage).
- Network Pillar: Cloud networks, firewalls, gateways, segmentation, and controls.
- Gathering data and mapping network traffic. This includes access controls, segmentation, remote access, network boundaries, and monitoring.
- Automation Pillar: Automation (SOAR) and reporting.
- Largely a recap of the advanced activities discussed in earlier pillars. This covers task automation, machine learning, AI, incident response, SOC, policies, and standards.
- Visibility Pillar: Security Information and Event Management (SIEM) layer.
- Much like the automation pillar, this pillar overlaps the earlier pillars. This covers centralization of security logs, correlating activities, UEBA, anomaly detection, and threat intelligence.
Solving Zero Trust with Microsoft Security (Simply Stated)
- User Pillar: Entra ID P2 with Identity Protection (MFA, conditional access, user risk scoring, PIM (Privileged Identity Management), dynamic groups, and access reviews); along with Defender for Identity (MDI) to protect on -prem Active Directory.
- Device Pillar: Defender for Endpoint (MDE) including Defender Antivirus in active mode along with Intune and GPOs for device configuration management and compliance.
- Application Pillar: Cloud hosted applications developed using DevSecOps best practices and cloud managed identities. Defender for Could for added app and infrastructure protection. Defender for Cloud Apps to extend conditional access to 3rd party apps.
- Data Pillar: Purview to provide data labeling and management. Office 365 Security (MDO) and Defender for Could Apps (MDCA) to enhance data loss prevention controls. Defender for Cloud for added database and storage protections.
- Network Pillar: Azure network security including NSGs (Network Security Groups), Azure Firewall, App Security Gateways, and segmentation through network design best practices. Monitored by Defender for Could and Sentinel. This may include on-premises network device log collection with Sentinel.
- Visibility & Automation Pillar: Sentinel provides SIEM, SOAR, UEBA, and threat intelligence.
Simply put, customers who are highly invested in Microsoft security solutions will meet most of the DOD Zero Trust requirements. Where 3rd party solutions are preferred, more care will be needed to review those affected pillars. The journey doesn’t stop there. Many DOD organizations have deployed these solutions to some degree. The next challenge is finishing deployments, activating features, resolving coverage gaps, increasing adoption, updating internal processes, migrating more capabilities to Azure, and applying a continuous improvement approach.
Special Considerations:
- Security technology is rapidly evolving, especially in terms of automation and artificial intelligence. The advanced pillars where some of the activities may not be ready now will be much easier to achieve as we draw closer to 2029.
- There are many practical and logistical reasons why Azure Government trails Azure Commercial in feature availability. DOD Zero Trust may be temporarily affected by these delays in some areas.
- There are a few activities that describe functionality that is not currently available from Microsoft. In most cases, these activities can be met by temporary workarounds or custom solutions.
Potential Microsoft Gaps
- File Integrity Monitoring:
- Defender for Cloud has a FIM solution that monitors key OS files for changes on servers. This may not be broad or deep enough to meet FIM requirements. This solution is being deprecated in preference for a future MDE-based solution. MDE currently tracks file activity but is not commonly described as a FIM solution.
- Automated device-level compliance scoring and blocking.
- Intune is needed for devices to report compliance for use in conditional access policies (comply-to-connect). These policies are rather basic including the lowest OS version, jail-break detection, and custom rules. This lacks a dynamic device risk or behavioral analytics capability to dynamically identify risky devices (natively). Though currently, a custom workaround would be possible.
- Blocking a user after they have successfully logged on due to detection.
- Once a user authenticates, SSO minimizes the need for re-verification. The desire for session, transaction-based, and continuous authentication discussed in some advanced activities may not be truly available today. There is no option to repeatedly analyze the risk of an authenticated session, kicking off the user when the risk increases. A custom workaround would be possible.
- UEBA alerting.
- User & Entity Behavioral Analytics (UEBA) and anomaly detection is often associated with Sentinel in the Microsoft stack; because Sentinel has a feature called UEBA. First, anomaly detection is present in most Azure security solutions (not just Sentinel). Second, Sentinel UEBA and Anomaly rules do not generate incidents (notifications) directly. Non-alerting auditing may not be considered detection. These datapoints are collected for enrichment and hunting. It is a common misconception that Sentinel will alert on anomalies directly (though adding alerting is simple if needed).
- Secure software development.
- The primary Microsoft solutions for secure software development (DevSecOps) have limited availability in Azure Government to date. Examples include Azure DevOps, GitHub, Defender for App Services, and Defender for APIs which are not yet available in Azure Government.
- Advanced AI and ML.
- Microsoft cloud security certainly has various forms of AI and ML. The advanced zero trust activities often involve some form of AI-ML. In some cases, these descriptions are future facing and native Microsoft solutions may lag in some AI-ML activities. Though we are confident these limitations will be addressed soon starting with Security for Copilot.
Microsoft Zero Trust by Pillar
The following section takes a closer look at the Microsoft solutions needed to address the DOD Zero Trust roadmap using Microsoft solutions.
User Pillar (Identity)
Entra ID (formerly AAD) is Microsoft’s cloud-based identity provider, further enhanced by Entra ID Identity Protection:
- Centralized management of user accounts and non-person identities including service principals and managed identities. Providing authentication for Microsoft and federates services, single sign-on, role-based access control.
- Integration with Active Directory to synchronize on-premises identities.
- Advanced sign-on protection through conditional access and multi-factor authentication (MFA). Including phishing resistant MFA, location blocking, smart lockout, password protection, and risk-based MFA based on dynamic user risk scoring.
- Self-service features allow users to securely reset passwords, register for MFA, and remediate conditional access blocks.
- Privileged Identity Management (PIM) provides a just-in-time solution for automated and manually approved, time-bound, privileged access requests.
- Dynamic groups minimize administrative overhead and lingering access for dynamic role-based access control.
- Maintain group membership using automated access reviews.
- Multi-tenant access delegation using guest accounts and Microsoft Lighthouse.
- Detailed reporting and logging and easy integration with Microsoft XDR and Sentinel.
Defender for Identity monitors on-premises domain controllers for a range of suspicious identity and network activity. Integrating on-premises identity protection with Defender XDR.
Device Pillar (Inventory & Protection)
Defender for Endpoint (MDE) is the cornerstone of device and server protection:
- Defender for Antivirus (MDAV) is Microsoft’s next-generation antivirus. Natively part of the modern Windows OS. MDAV includes real-time scanning, best-in-class threat intelligence, cloud-based file detonation, behavioral analytics, and works side-by-side with 3rd party AV when present.
- Protecting devices (desktops, laptops, phones, tablets) and servers running Windows, Linux, MacOS, Android, and IOS.
- MDAV goes beyond traditional antivirus by blocking suspicious network connections and websites (from any browser).
- Automated Investigation & Response automatically resolves a growing number of device security issues with no human involvement.
- MDE inventories users and applications for each device, providing insights into software-based risks and vulnerabilities through prioritized recommendations.
- Continuous assessment of device configuration, providing device hardening recommendations and compliance.
- Extended protections include exploit guard, ASR Rule tracking, web content filtering, application control, device control (blocking external devices), controlled folder access (ransomware protection), and more.
- Device Discovery uses the MDE client as a proxy to discover unmanaged devices, rogue devices, network equipment, and IOT/OT.
- MDE supports monitoring and un-managed device management (BYOD).
- Incident response tools to remotely access, isolate, run AV scans, capture configuration snapshots, and run custom security scripts.
- Detailed device activity audit logging and easy integration with Microsoft Sentinel and strong integrations with Defender for Cloud, Defender for IoT, Defender for Cloud Apps, and Intune.
Defender XDR is the web portal (security.microsoft.com or security.microsoft.us) to centrally managed Defender for Endpoint, Defender for Office, Defender for Could Apps, and Defender for Identity.
- Natively integrated with Entra ID Identity Protection and Purview alerts.
- Automatically grouping alerts from MDE, MDO, MDCA, MDI, Entra ID, and Purview (most based on a common license model) into a single incident based on common timelines and entities. Providing a more complete picture of suspicious behavior and reducing duplication of effort.
- Provides free 2-way alert integration with Microsoft Sentinel and discounted data integration for E5\A5 users.
- Soon to be the primary incident management solution for Sentinel and XDR called the Unified Security Operations Platform.
- Soon to be a primary method for using Copilot for Security that will provide a private, generative AI chatbot to guide incident responders.
Intune is a cloud-based software distribution and patching solution:
- Provides an inventory of managed devices and automatically joins devices to Entra ID (required for devices to use Intune).
- Provides cloud-based policy management of devices with detailed compliance reporting (modern GPO). Intune is the recommended policy service for MDE.
- Intune compliance policies can be used to identify non-compliance devices, integrated with Entra ID conditional access to block non-compliant devices (C2C).
- Provides an alternative method to remotely disable managed devices.
- Integrates with Microsoft Endpoint Configuration Manager (MECM) to co-manage on-premises devices, streamlining cloud migration.
Defender for Cloud protects your Azure subscriptions and Azure resources (VMs, storage accounts, containers, and more):
- Defender for Servers alerts on unusual remote access attempts and provides hardening recommendations (secure score) for Azure VMs and servers outside of Azure (on-premises) connected over Azure Arc.
- Defender for Servers can recommend network access improvements and provide just-in-time RDP access for Azure VMs.
- Defender for Servers includes an MDE for Servers license and can automatically onboard servers to MDE.
- Defender for Databases provides specific alerts and hardening recommendations for Azure and databases outside of Azure connected over Azure Arc.
Defender for IoT provides added protection (in addition to MDE) for Operational Technology (OT) and IoT devices. Helping to identify suspicious network communication and device inventory for connected and air–gapped OT/IoT.
Application Pilar – Inventory & Secure Development
Azure DevOps (not available in Gov yet) allows organizations to create and improve products at a faster pace than they can with traditional software development approaches including job boards, GIT repositories, pipelines, and test plans.
GitHub (not available in Gov yet) enables organizations to plan, share, collaborate, and maintain software development pipelines. GitHub can also be used to create a Software Bill of Materials (SBOM).
GitHub Copilot for Enterprise (not available in Gov yet) builds the power of generative AI into an editor extension that suggests code in real-time. GitHub Copilot for Business and Enterprise adds more powerful AI, security, and management controls for enterprise project teams.
Visual Studio is a powerful developer tool that you can use to complete the entire development cycle in one place. It is a comprehensive integrated development environment (IDE) that you can use to write, edit, debug, and build code, and then deploy your app.
Power Platform is a suite of apps, services, and connectors, as well as a data platform, that provides a rapid development environment to build custom apps for your business needs securely.
Defender for Cloud Apps (MDCA) discovers and monitors cloud application usage.
- Using an agentless reverse proxy, Entra ID Conditional Access and Intune device compliance can be used secure access to web applications.
- MDCA can identify web applications as sanctioned or unsanctioned and can block access to unsanctioned apps using MDE, supported 3rd party firewalls, and conditional access.
Azrue Key Vault provides cloud-based key, secret, and digital certificate management. Secrets used for application and API security, centralized key rotation, encryption, and more.
Windows Defender Applicaiton Control (WDAC) provides the ability to block the installation of unauthorized software that initially trusts Microsoft and organizational software distribution services like MECM. Also, MDE supports the blocking of Potentially Unwanted Applications (PUA)
Defender for Cloud protects your Azure subscriptions and Azure resources (VMs, storage accounts, containers, and more):
- Defender for Key Vault advanced threat protection for Azure Key Vault, providing an added layer of security intelligence.
- Defender for Containers is a cloud-native solution to improve, monitor, and maintain the security of your containerized assets (Kubernetes clusters, Kubernetes nodes, Kubernetes workloads, container registries, container images and more), and their applications, across multi-cloud and on-premises environments.
- Defender for App Service (not available in Gov yet) assesses the resources covered by your Azure App Service plans and generates security recommendations based on its findings.
- Defender for APIs (not available in Gov yet) offers full lifecycle protection, detection, and response coverage for APIs.
Azure Open AI provide plug-and play AI solutions for developers to tap into powerful artificial intelligence capabilities with minimal development effort while maintaining safety and privacy. Not to be confused with Copilot for Security which is a generative AI service.
Data Pillar – Inventory and Governance of Data
Purview is a comprehensive set of solutions that can help your organization govern, protect, and manage data, wherever it lives.
- Securing data through labeling, mapping, and auditing to provide data loss prevention, information protection, data barriers, access management, and lifecycle management.
- Alert on unusual activity using the Defender XDR portal.
- Enhanced DLP solutions in Office 365 and Defender for Cloud Apps to block sensitive file sharing through email, Office 365, and web apps.
Defender for Cloud Apps (MDCA) discovers and monitors cloud application usage.
- Using an agentless reverse proxy, Entra ID Conditional Access and Intune device compliance can be used secure access to web applications.
- MDCA can identify web applications as sanctioned or unsanctioned and can block access to unsanctioned apps using MDE, supported 3rd party firewalls, and conditional access.
Defender for Office 365 protects against phishing, malware, spam, and business email compromise and covers Microsoft Teams, SharePoint, OneDrive, and Office apps.
- Detailed logging of Office 365 activity with easy integration with Defender XDR and Sentinel for incident response, hunting, and archival.
- Create user training campaigns using fictitious social engineering emails.
Defender for Cloud protects your Azure subscriptions and Azure resources (VMs, storage accounts, containers, and more):
- Defender for Databases allows you to protect your entire database estate with attack detection and threat response for the most popular database types (both in Azure and outside of Azure). Not available for database outside of Azure currently for Aure Government.
Encryption at Rest is natively part of Azure. This includes storage accounts, virtual disks, workspaces, data lakes, and databases. All are encrypted at rest, often with redundancy, using Microsoft managed keys or customer managed keys (if needed).
Encryption in Transit is also natively part of Azure. All Microsoft managed connections are encrypted using Transport Layer Security TLS1.2 encryption.
Network Pillar – Monitoring & Protecting the Network
Network Design is a big part of the network pillar, primarily micro and macro network segmentation. The line between Aure networking and on-premises here can be unclear.
Express Route extends your on-premises networks into the Microsoft cloud over a secure, private connection. Connectivity can be from an any-to-any (IP VPN) network, a point-to-point Ethernet network, or a virtual cross-connection through a connectivity provider at a colocation facility.
Secure Azure Computing Architecture (SACA) describes the functional goals for securing the Defense Information System Network’s (DISN) and commercial cloud provider connection points. This includes the Boundary Cloud Access Point (BCAP). The BCAP protects the DISN from attacks originating in the cloud environment. BCAP performs intrusion detection and prevention. It also filters out unauthorized traffic.
Azure Firewall is a cloud-native, next-generation, and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
- Includes Azure Application Gateway (managed web traffic load balancer and reverse proxy) and Azure Web Application Firewall adds HTTP inspection and protections for App Gateway.
- Includes the ability to provide threat intelligence and ransomware protection at the network perimeter.
Network Security Groups (NSG) filter network traffic between Azure resources in an Azure virtual network. A network security group has security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
Azure DNS is a hosting service for DNS domains that provides name resolution by using Microsoft Azure infrastructure. By hosting your domains in Azure, you can manage your DNS records by using the same credentials, APIs, tools, and billing as your other Azure services
Azure DDoS Protection is a service that protects Azure resources from distributed denial-of-service (DDoS) attacks. It uses Azure’s global deployment scale and offers 60Tbps of global attack mitigation capacity. Though all Aure resources inherit a reasonable level of DDoS protection natively.
Defender for Identity (MDI) monitors on-premises domain controllers for a range of suspicious identity and network activity. Integrating on-premises identity protection with Defender XDR.
- MDI inspects network requests sent to domain controllers and can detect network-based reconnaissance activity targeted at DNS and LDAP.
Defender for Cloud protects your Azure subscriptions and Azure resources (VMs, storage accounts, containers, and more):
- Defender for Servers provider visual network maps of network communication to Azure Virtual Servers (VMs). Similar information is provided by Aure Monitor VM Insights.
- Defender for Servers includes Adaptive Network Hardening that recommends NSG rule improvements to harden VM networks. Limited to VMs behind firewalls and despite the name, this is not an automated solution (blocking is manual).
- Defender for DNS monitors the queries from these resources and detects suspicious activities without the need for any additional agents on your resources. This service has been rolled into Defender for Servers (not a standalone offer).
- Defender for Cloud finds internet facing VMs, storage accounts, and resources, providing additional recommendations on network hardening.
Microsoft Sentinel adds the ability to centralize network activity logs from a wide range of sources including Azure and on-premises network devices. Creating a central repository for alert monitoring and threat intelligence (detecting indicators of compromise).
- Sentinel Threat Intelligence provides customers with multiple ways to collect, store, and apply threat intelligence (indicators of compromise) from Microsoft and 3rd party sources at scale.
Automation Pillar (SOAR)
Microsoft Sentinel is your gateway to security automation including enrichment, notification, incident triage, remediation (response), and process automation.
Microsoft Serverless Automation:
- Logic Apps automated API-based workflows with little to no code. Simplifying integration between web-based applications using hundreds of built-in connectors. Custom, inexpensive, secure automation that can be created and maintained by novice developers. Sentinel automation (playbooks) run on logic apps.
- Azure Functions are a serverless solution for running scripts developed in C#, Java, JavaScript, PowerShell, and Python. Capable of the same types of solutions created using logic apps and more, only faster, cheaper, and higher capacity though requiring developer skills.
- Power Automate allows users to create workflows (flows) that are like logic apps but more user or team focused within Office 365. Part of the Power Platform service; used for low-code app development.
- Azure Automation Azure Automation delivers cloud-based automation, operating system updates, and configuration service that supports consistent management across your Azure and non-Azure environments. The service allows you to author graphical, PowerShell and Python runbooks and supports PowerShell desired state configuration (DSC).
Azur Security APIs are available for every Microsoft security solution, allowing for custom development, system integration, and automation.
Defender for Endpoint (MDE) includes Auto Investigation & Response (AIR) which takes immediate action to resolve breaches. AIR can remove a registry key, kill a process, stop a service, disable a driver, or remove a scheduled task automatically as an alert response. No custom development needed.
Azure Policy automates Azure resource governance by tracking or enforcing configuration settings. Preventing and tracking of non-compliant settings (custom secure by default).
Entra ID automated risky user detection, provides user with self-service tools to reset passwords/MFA, just-in-time privileged access, and more. Greatly reducing the need for custom automation related to identity lifecycle management.
Visibility (SIEM)
Microsoft Sentinel is a cloud-native Security Information & Event Management (SIE) solution. Most of pillars 6-7 goals are provided by Sentinel.
- Data Connectors simplify the collection of security logs from a broad range of sources. Sentinel also provides a framework for custom connector development.
- Log Analytics Workspace provides a cloud-native repository for log data storage with near limitless scale. With 90-days of retention included, up to 2 years of hot storage and 12 years of data archival capacity.
- Data Export allows for table-level data migrations to long term archival solutions or 3rd party datastores including blob storage, event hub, Azure Data Explorer (ADX)< and Azure Data Lake Services (ADLS).
- Workbooks in Sentinel provide serverless dashboards that are highly customizable and easily imported as templates. Visualization is further enhanced by Azure Dashboards, PowerBI, and Grafana managed instance for more specific use cases.
- Analytic Rules in Sentinel provide highly customizable alerting. Adding custom detections to Microsoft security services and custom tables.
- Notebooks in Sentinel provide a framework for Jupyter Notebooks written in Python for machine learning, visualization, and data analysis. Sentinel provides templates and compute resources for this advanced form of automation. Though in practice, Sentinel Notebooks are not required to meet ZT objectives.
- Machine Learning is provided in Sentinel:
- User & Entity Behavior Analytics (UEBA) finds user, host, and IP related anomalies using specific Sentinel data. These insights are recorded for hunting and shared with Fusion. Note that Sentinel UEBA is non-alerting by default and UEBA is not exclusive to Sentinel.
- Anomaly Rules in Sentinel look for similar anomalous activity by evaluating scenarios not limited to traditional UEBA entities. Like UEBA, these are non-alerting insights that are recorded for hunting and shared with Fusion.
- Multistage Attack Detection (Fusion) is a single analytic rule in Sentinel that represents over 120 advanced detections. Each detection involves two indicators in close succession, representing a known attack path. For example, risky sign-on followed by privileged action. Fusion uses inputs from several Sentinel data sources, UEBA, and Microsoft threat intelligence.
Defender XDR is the web portal (security.microsoft.com or security.microsoft.us) to centrally managed Defender for Endpoint, Defender for Office, Defender for Could Apps, and Defender for Identity.
- Defender XDR plays a critical role in security visualization. Though not officially considered a SIEM, this portal provides extensive visualization on the Microsoft security stack including 180-days of reporting data (30-days hunting).
- Defender XDR has strong integration with Sentinel for 2-way incident synchronization and long-term data archival. These two services will only become more tightly integrated into the Unified SOC Platform.
Key References
- DOD Zero Trust Executive Roadmap
- DOD Zero Trust Activities List
- Microsoft Feature Availability for US Government
- Defender XDR for US Government
- Security Copilot for US Government
- Azure Well Architected Framework
Microsoft DOD Zero Trust Checklist
The following table is a sample tracker for recording the status of various DOD Zero Trust affecting solutions. Individual items can be added, removed, combined, or expanded as needed. For zero trust, when speaking in terms of “all” we assume any exceptions are documented and authorized by a formal process. There will always be some exceptions.
| Solution | Deployment | Adoption | Maturity | Pillars |
| Entra ID is primary IDP | 1 | |||
| All users are Entra IDP P2 | 1 | |||
| All user-sign-on requires MFA | 1 | |||
| Conditional Access | 1 | |||
| Risk-based conditional access | 1 | |||
| MDCA conditional access | 1 | |||
| Periodically review CA policies | 1 | |||
| SSPR and MFA enrollment | 1 | |||
| Privileged access requires PIM | 1 | |||
| Dynamic Groups used for RBAC | 1 | |||
| Entra Access Reviews | 1 | |||
| Sync on-prem AD (AD Sync) | 1 | |||
| MDI on all domain controllers | 1,5 | |||
| Periodic review of least privileged | 1 | |||
| Identity lifecycle for all identities | 1 | |||
| Automated identity lifecycle mgmt. | 1 | |||
| Process to cleanup stale identities | 1 | |||
| Periodically review delegated access | 1 | |||
| Lighthouse used over guest accounts | 1 | |||
| MDE in active mode on all devices | 2 | |||
| MDAV policy is fully managed | 2 | |||
| MDAV potentially unwanted apps (PUA) | 2 | |||
| MDE response tools are in use | 2 | |||
| MDE recommendations are triaged | 2 | |||
| Device discovery used for rouge/IoT | 2,5 | |||
| Web & network protection | 2,3 | |||
| MDE web content filtering | 2,3 | |||
| Device control (limit or audit external media) | 2 | |||
| Exploit Guard enabled on all Windows OS | 2 | |||
| ASR rule auditing and enforcement | 2 | |||
| Auto Investigation (AIR) full-auto | 2,6 | |||
| MDE file detonation enabled | 2 | |||
| Application control (only allow approved) | 2,3 | |||
| All Windows/Linux/MacOS are managed by Intine\MECM | 1,2 | |||
| BYOD protected if allowed | 2 | |||
| Def for Office 365 in use | 2 | |||
| MDCA in use | 2,3 | |||
| Intune compliance/conditional access (C2) | 1,2 | |||
| All available Def for Cloud services enabled | 2,3,4,5 | |||
| Defender for Servers | 2 | |||
| Defender for Database | 4 | |||
| Defender for Storage | 4 | |||
| Defender for Containers | 3 | |||
| Purview | 4 | |||
| Defender for IoT | 2,5 | |||
| DDOS Protection | 3,5 | |||
| Azure DevOps or GitHub for DevSecOps | 3 | |||
| Visual Studios for development | 3 | |||
| Azure Key Vault for app keys | 1,3 | |||
| Power Platform for internal apps | 3 | |||
| Express Route or BCAP | 4 | |||
| Azure Firewall (App Gateway) | 4 | |||
| Segmented network design | 4 | |||
| Sentinel is the primary SIEM | 1-7 | |||
| Sentinel UEBA enabled | 6-7 | |||
| Sentinel Threat Intelligence | 1-7 | |||
| All related data connectors enabled | 7 | |||
| Sentinel Playbooks are used | 6 | |||
| Dashboards (workbooks and PowerBI) | 7 |
Deeper Look at Zero Trust Pillars
User Pillar
- User accounts and their access are inventoried (unauthorized users are denied) [AAD RBAC & AD Sync].
- Conditional user access based on dynamic risk criteria [AAD P2 Conditional Access].
- Users and non-user identities require MFA [AAD and Key Vault]. Note that non-user identities (APIs, managed identities, and service principals) generally do not take part in MFA, though the credentials can be highly secure.
- Privileged Access Management (PAM) or just-in-time admin access [AAD P2 PIM].
- Centralized account federation for centralized control and SSO [AAD].
- Standardizing the Identity Lifecycle Management (ILM) processes [AAD Dynamic Groups & Access Reviews].
- UEBA is used in deciding user risk levels [AAD Identity Protection].
- Biometric telemetry to enhance risk-based authentication [Possibly MFA related risk score, AAD Identity Protection].
- Least Privileged Access to include auto removal when no longer needed [AAD Dynamic Groups & Access Reviews, PIM].
- Continuous user authentication [Conditional access & MFA].
- Identity, Credential, and Access Management (ICAM) integrated platform (enterprise-level identity management, PKI, and federation) [AAD & Key Vault].
Device Pillar
- Devices are inventoried and enrolled in a management service [AD, AAD, MDE, MDFC, Intune, MECM].
- Managed devices are enrolled in an asset management system that reports on compliance [MDE, MDFC, & Intune].
- Compliance and enrollment in device management checked before connecting [AD, AAD, Intune device-level conditional access].
- Devices have Next Gen Antivirus [MDE, MDAV].
- Devices have file integrity monitoring [MDE & MDFC]. Note that this might be a weak area depending on how FIM is described.
- Device real-time inspection and risk scoring/assessment [MDE & MDFC]. Note that servers and user devices may have different solutions/requirements.
- Expand the existing Enterprise PKI to devices as well [possibly Key Vault]. Note that device-level PKI might not be applicable.
- Remote access to the agency network (VPN/BYOD) or public-facing apps [Office 365].
- Hybrid manual and automated patching of devices [Intune, MECM, Azure Arc]. Note that this includes testing and deployment.
- Remote management and policy enforcement (agent or agentless) for computers and user devices [MDE & Intune].
- EDR & XDR [MDE, MDFC, & Intune].
Applications Pillar
- All applications and application components are identified and inventoried.
- Only authorized applications are allowed.
- Applications are held to a zero trust standard (code review, runtime protection, secure API gateways, container and serverless security).
- Custom software development teams use DevSecOps (CICD pipeline).
- Establish software/application risk management program.
- Software Bill of Materials (SBOM) and approved repositories.
- Supplier Risk Management & vulnerability management program.
- Establishes a standard approach to managing the authorizations of resources.
- Continuously monitor applications and assess their authorization to operate.
Data Pillar [Mainly Purview]
- Data is identified and inventoried and any changes to the data landscape are automatically detected.
- Data landscape reviewed to identify potential risks (data loss, attack, unauthorized activity).
- Data assets are known (collected & tagged according to risk levels) and encrypted for protection.
- Enforced data labeling/tagging (per DoD policy) and access control/sharing policies.
- Data tagging should have both manual and automated controls.
- Ensure an appropriate level of sharing between DoD Organizations.
- Monitor access, sharing, transformation, and use of their data assets.
- Data Loss Prevention (DLP).
- Data Rights Management (DRM).
- Monitor any File Shares and Databases that are out of DLP\DRM scope.
- Software Defined Storage (SDS) Policy.
- File and database activity monitoring (which implies cloud storage as well).
- Encrypting data at rest and in transit.
- Automate protection using ML and AI (advanced).
- Ensure appropriate access to and use of data (managing permissions).
- Unauthorized users/devices are unable to access data.
Network Pillar
- Gathering, mapping, and visualizing network traffic to understand data flows.
- Ensure authorized access and protection for network activity.
- Employ network segmentation best practices (separate the control and data planes).
- Software Defined Networking (SDN) – real time decision making for access to resources.
- Establish network boundaries and secure by validating remote connections before allowed.
- Implement Micro segmentation (narrower and specific segmentation).
- Real-time access decisions and policy changes.
- Monitoring of network activity and network threat intelligence.
Automation Pillar
- Collect and document all rule-based policies.
- Defined, implemented, and updated access procedures and policies.
- Enable, monitor, and terminate connections according to predefined policy.
- Security related policy-based management (Azure Policy, GPO, Intune).
- Automate repetitive, predictable tasks for critical functions such as data enrichment, security controls, and incident response.
- Employ ML for incident response, anomaly detection, user baselining, and data tagging.
- Employ AI in risk and access determinations analysis.
- SOAR – triggering automation for incident response.
- Establish API standards and all non-compliant APIs are identified and replaced.
- Establish a SOC or outsource to a reputable service provider.
- Standardized, coordinated, and accelerated incident response and investigative efforts.
Visibility Pillar [Mainly Sentinel]
- Collect and process all logs including network, data, application, device, and user logs.
- Make those logs available to the appropriate service provider [JFHQ DODIN] and SOC.
- Monitor, detect, and analyze data logged into a SIEM.
- User and device baselines are created using security controls.
- Service provider or SOC examined events, activities, and behaviors.
- Correlate user activities and behaviors and detect anomalies (UEBA).
- Integrate threat intelligence and TTP [MITRE] with data collected in the SIEM.
- ML & AI solutions dynamically and automatically update security profiles.
Zero Trust Capabilities Reference
Users (28 activities):
- 1.1 User Inventory
- 1.2 Conditional User Access
- 1.3 Multi-Factor Authentication (MFA)
- 1.4 Privileged Access Management (PAM)
- 1.5 Identity Federation & User Credentialing
- 1.6 Behavioral, Contextual ID, and Biometrics
- 1.7 Least Privileged Access
- 1.8 Continuous Authentication
- 1.9 Integrated ICAM Platform
Devices (24 activities):
- 2.1 Device Inventory
- 2.2 Device Detection and Compliance
- 2.3 Device Authorization w/ Real Time Inspection
- 2.4 Remote Access
- 2.5 Partially & Fully Automated Asset, Vulnerability and Patch Management
- 2.6 Unified Endpoint Management (UEM) & Mobile Device Management (MDM)
- 2.7 Endpoint & Extended Detection & Response (EDR & XDR)
Applications (18 activities):
- 3.1 Application Inventory
- 3.4 Resource Authorization & Integration
- 3.2 Secure Software Development & Integration
- 3.3 Software Risk Management
- 3.5 Continuous Monitoring and Ongoing Authorizations
Data (31 activities):
- 4.1 Data Catalog Risk Alignment
- 4.2 DoD Enterprise Data Governance
- 4.3 Data Labeling and Tagging
- 4.4 Data Monitoring and Sensing
- 4.5 Data Encryption & Rights Management
- 4.6 Data Loss Prevention (DLP)
- 4.7 Data Access Control
Network (13 activities):
- 5.1 Data Flow Mapping
- 5.2 Software Defined Networking (SDN)
- 5.3 Macro Segmentation
- 5.4 Micro Segmentation
Automation (20 activities):
- 6.1 Policy Decision Point (PDP) & Policy Orchestration
- 6.2 Critical Process Automation
- 6.3 Machine Learning
- 6.4 Artificial Intelligence
- 6.5 Security Orchestration, Automation & Response (SOAR)
- 6.6 API Standardization
- 6.7 Security Operations Center (SOC) & Incident Response (IR)
Visibility (18 activities):
- 7.1 Log All Traffic (Network, Data, Apps, Users)
- 7.2 Security Information and Event Management (SIEM)
- 7.3 Common Security and Risk Analytics
- 7.4 User and Entity Behavior Analytics
- 7.5 Threat Intelligence Integration
- 7.6 Automated Dynamic Policies
Related Terms
Bring Your Own Device (BYOD) refers to being allowed to use one’s personally owned device, rather than being required to use an officially provided device. Also referred to unmanaged devices. Examples may include laptops, tablets, and cell phones. BYOD can securely access resources using applications, portals, websites, and VPNs.
Comply-to-Connect (C2C) refers to multiple services that ensure users and devices must comply with policies to connect. Microsoft examples include conditional access and Intune device compliance policy.
Credential and Access Management (ICAM) creates a secure and trusted environment where any user can access all authorized resources to have a successful mission, while also letting the Department of Defense (DoD) know who is on the network at any given time. ICAM is not a single process or technology but is a complex set of systems and services that run under varying policies and organizations. Though the primary
Cyber Threat Intelligence (CTI) refers to the collection and application of various indicators of compromise (IOCs) to find potentially malicious activity. Indicators collected through research or more likely acquired from security vendors and government agencies. These indicators may include IP addresses, domain names, file names (or hashes), and more in combination with a SIEM or XDR to detect and response to suspicious activity.
Data Loss Prevention (DLP) is the process of protecting and preventing sensitive data from being lost, stolen, or compromised. Often DLP is associated with insider threats (employees and contractors). The Microsoft solutions include Purview, Microsoft Cloud App Security (MCAS), and Microsoft 365.
Data Rights Management (DRM) focuses on file and data permissions, sharing, and auditing. Often associated with data labeling and tagging. The Microsoft solution for DRM is Purview.
DDIL is a military term for disconnected, denied, intermittent and low bandwidth. Also referred to as “edge” networks or devices. Examples may include naval ships, air gapped networks, and geographically isolated locations with limited bandwidth.
Extended Detection & Response (XDR) is a holistic security solution. Generally considered to focus on end-user devices. Combining services like auditing (logging), reporting, antivirus, venerability assessment, configuration management, file integrity monitoring, inventory management, incident response, and more into a single solution. The Microsoft XDR portal brings together MDE, MDAV, MDO, MDI, MDCA, and more to provide an XDR solution.
File Integrity Monitoring (FIM) audits changes to system files and can be used to detect and possibly recover unauthorized changes. This may be limited to critical files or may broadly audit all files on a disk, folder, or repository. This may involve baseline versions and anomaly detection. Generally focused on the prevention of operating system file changes, rather than sensitive file monitoring (tagging).
Identity Provider (IdP) is a service that creates, maintains, and manages identity information for principals and provides authentication services to applications within a federation or distributed network. For example, Entra ID and Active Directory.
Multifactor Authentication (MFA) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence to an authentication mechanism.
National INstitute of Standards & Technology (NIST) is a federal agency that supports innovation, resilience and competitiveness in the U.S. economy and society. Known for related services including the National Vulnerability Database (NVD), Common Vulnerabilities (CVE’s), and the NIST 800-53 regulatory compliance standard.
Privileged Access Management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. PAM works through a combination of people, processes, and technology and gives you visibility into who is using privileged accounts and what they are doing while they are logged in. PAM is often associated with Entra ID PIM; though PAM is a much broader concept.
Privileged identity management (PIM) is a service in Microsoft Entra ID that enables you to manage, control, and monitor access to important resources in your organization. PIM provides an approval process and auditing for temporary privileged access requests. Providing time bound, just-in-time, privileged access.
Public Key Infrastructure (PKI) refers to the services that support public key (certificate-based) authentication. Traditionally this includes Certificate Authority servers and Certificate Revocation Lists. The primary Microsoft Azure solution is Azure Key Vault.
Security Information & Event Management (SIEM) is a technology designed to centralize security logs and alerts to provide a hub for incident detection, reporting, anomaly detection, investigation (hunting), and archival. Often characterized by broad data collection capabilities, massive data ingestion and storage, dashboards, and tools make use of large datasets. Microsoft Sentinel is Microsoft’s cloud native SIEM solution.
Security Orchestration, Automation and Response solution (SOAR) is an orchestration service for security related automation including enrichment, notification, and recovery. Microsoft Sentinel is also Microsoft’s cloud native SOAR solution.
Software Defined Storage (SDS) is a marketing term for computer data storage software for policy-based provisioning and management of data storage independent of the underlying hardware. Microsoft SDS solutions include Azure Blob Storage and One Drive.
Service Oriented Architecture (SOA) defines a method to make software components reusable and interoperable. Services use common interface (API) standards and an architectural pattern so they can be rapidly incorporated into new applications.
User Activity Monitoring (UAM) is the technical capability to observe and record the actions and activities of an individual, at any time, on any device accessing U.S. Government information to detect insider threats and to support investigations. Examples may include web browsing, file access, web application usage, executed commands, etc. UAM may also imply detection of unusual behavior using machine learning. Microsoft examples include Purview, Defender for Endpoint, and Defender for Could Apps.
User & Entity Behavior Analytics (UEBA) finds unusual trends (anomalies) for key users and entity activities like logons, IP communication, location, usage, and more. Often associated with artificial intelligence and machine learning. Examples may include impossible travel, actions unrelate to job role, and unusual access patterns. Microsoft examples include Sentinel UEBA and risk-based conditional access policies (Entra ID).
Non-Person Entities (NPEs) are non-human actors. This can include organizations, hardware devices, software applications, and information artifacts. For zero trust, NPE examples include devices, apps, APIs and the associated identities.
Unified Endpoint and Device Management (UEDM) is a centralized solution monitor, manage and secure an organization’s end-user devices (desktops and laptops, smartphones, tablets) and servers. For Microsoft this would be Defender for Endpoint with support from Intune, Microsoft Endpoint Configuration Manager (MECM), and GPO.
Zero Trust Reference Architecture (ZTRA) Provides an end-state vision, strategy, and framework for Mission Owners across the DoD to strengthen cybersecurity and guide the evolution of existing capabilities to focus on a data-centric strategy.